1. Connect an Application
Connect the first application you want to manage. You can find instructions for each application in the integrations overview.Pre-built integrations
Custom integrations
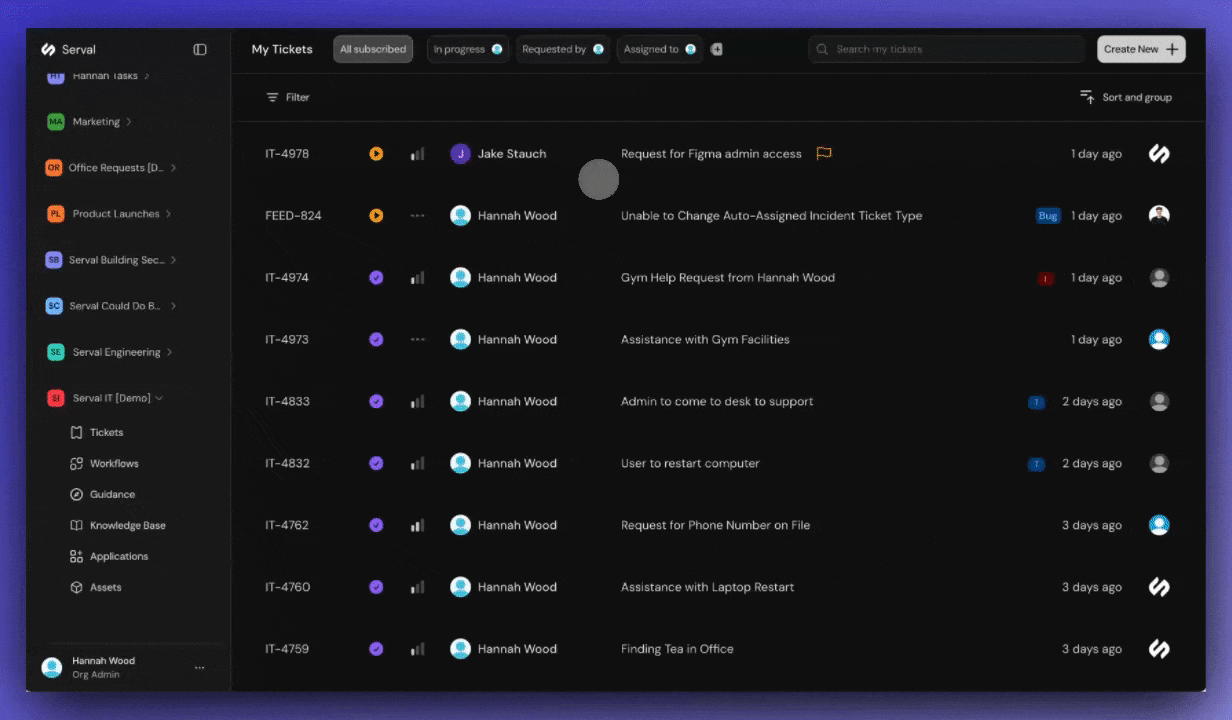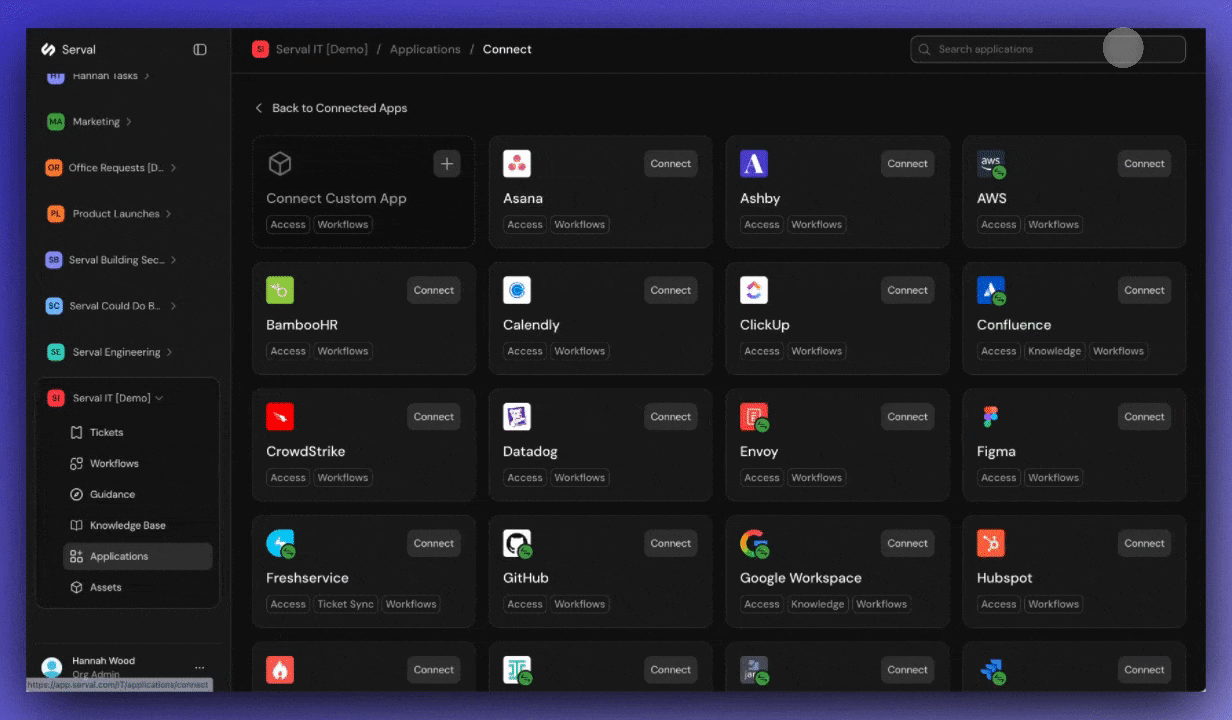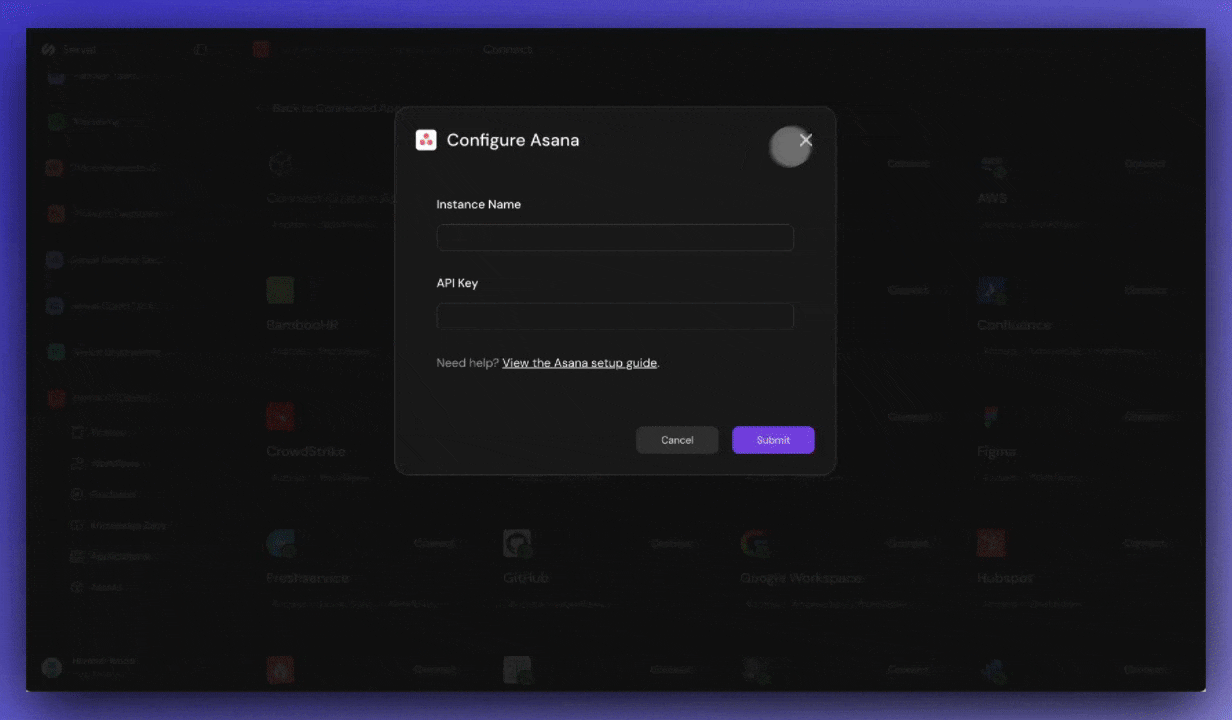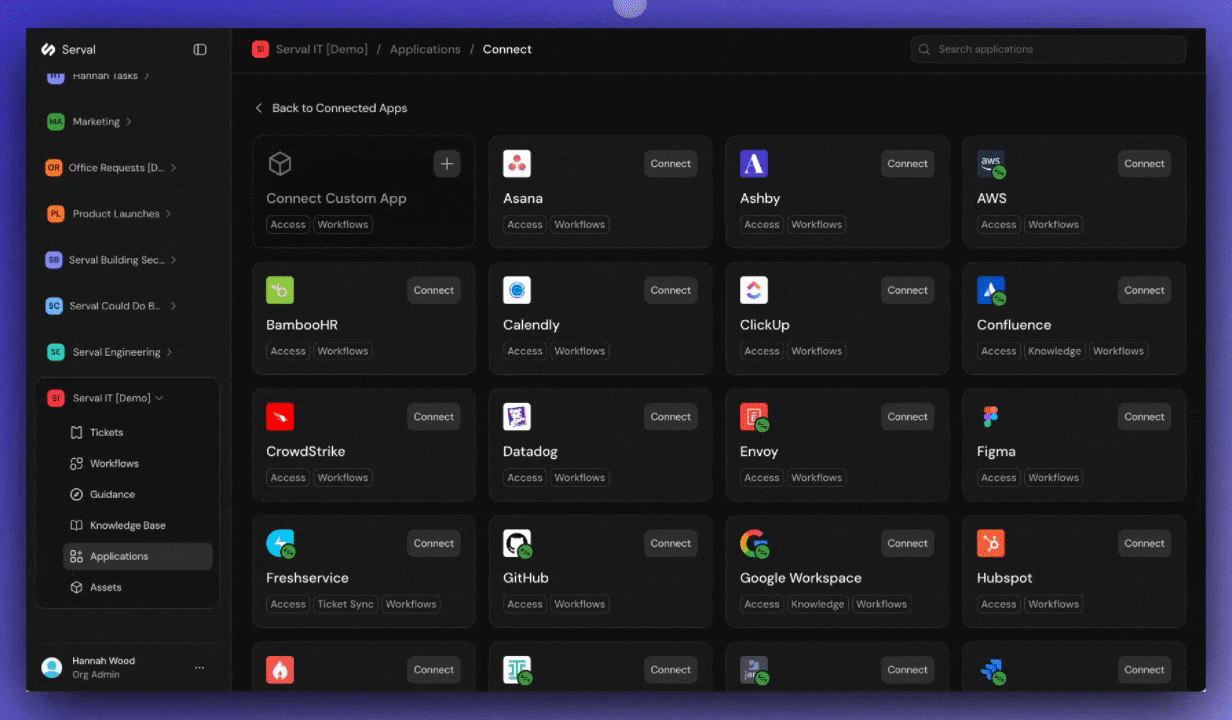
2. Configure Roles
Navigate to the application you’d like to configure access to and identify which roles you’d like to configure first.Access layers
In Serval, you can configure role access at two levels:Application roles
Resource roles
Configure roles three ways
Serval offers manual role setup (most common), importing roles from your IdP, and auto-filled roles.Manually configuring roles
Navigate to the relevant team from the sidebar, click Applications, then select the relevant application. Creating rolesAdd a new role
- For application roles: Click “New Role” in “App Access”
- For resource roles:
- Click “Create a Custom Resource,” fill in the Name and Description, then click “New Role” in that resource
- Click into an existing resource and click “New Role” in that resource
Configure role details
- Name the role (e.g., Member, Admin, Editor)
- Add a description of what type of access this is. Serval will use this to guide users to the right access level
Set up access controls
- Access Profiles: Which groups can request this role
- Access Policies: Rules for access requests (duration, business justification, approval process)
- Provisioning Methods: How access is granted (manual task, SCIM, custom workflow, API)
Importing roles from your IdP
Once you’ve connected an IdP to Serval, Serval will populate suggested roles based on the groups you have set up in that IdP.- Serval matches IdP group names to potential roles and lets you import them.
- After importing a role, configure provisioning through Linked Groups, Custom Workflows, or Direct (via API).
Auto-filled roles
For Linear and Ramp, Serval automatically identifies default application roles and adds them upon connection.- Navigate to the application
- Configure each auto-filled role with the appropriate profiles, policies, and provisioning methods.
3. Test Access Requests
Use your configured help desk (or the ticketing system in app.serval.com) to verify your setup works as intended.Submit a test request
Verify the workflow
- The request routes to the correct approver
- Business justification requirements work as expected
- Access is provisioned correctly
- Temporary access expires on schedule
4. Audit and Monitor Access
Once your access management system is in use, monitor access and view access logs to ensure compliance and identify potential security issues. Learn more about access reviews here.5. Manage Profiles and Policies Centrally
Manage profiles and policies centrally to maintain uniform access controls across your organization. See access profiles and access policies for details. Navigate to the relevant team, click the ”…” button at the top right corner of the relevant team you’re managing, then select “access profiles” or “access policies.” From this view, you can:- Set default profiles and policies
- Configure centralized access controls
- Manage role assignments
Special Cases
IdP groups as resources
IdP groups as resources
Applications to exclude from access management
Applications to exclude from access management
- Slack channels
- Google groups
- Okta groups
- Email distribution lists
Example Scenario: Starter use case for access management
Your organization uses Okta, Google, Slack, and GitHub. Your Engineering team uses AWS databases.- Connect your IdP and help desk to Serval
- Configure application and resource access for company-wide and team-specific resources
- Define access policies with approval workflows and provisioning methods
- Name: GitHub - Member
- Description: Standard user access
- Policy: Indefinite access, no approval required
- Provisioning: Linked Group - add user to “Engineering” group in Okta
- Name: GitHub Engineering Team - Administrator
- Description: Full admin access to manage repos in GitHub Engineering Team
- Policy: Seven-day temporary access, requires Engineering Manager approval
- Provisioning: API provisioning through GitHub
Best practices
Connect your IdP first
Centralize to fewer teams
Create reusable policies
Verify with test requests
Review logs regularly
FAQs
Is Serval a Privileged Access Manager (PAM)?
Is Serval a Privileged Access Manager (PAM)?
What's the difference between Access Profiles and Access Policies?
What's the difference between Access Profiles and Access Policies?
Does Serval replace my identity provider (IdP)?
Does Serval replace my identity provider (IdP)?
How long does it take for access to be provisioned?
How long does it take for access to be provisioned?
- Direct provisioning: Seconds
- Linked Groups: 15 minutes to 1 hour, depending on your IdP’s sync schedule
- Custom Workflows: Varies based on workflow complexity
- Manual provisioning: Depends on human response time
What happens when temporary access expires?
What happens when temporary access expires?
Can I use different provisioning methods for different roles in the same app?
Can I use different provisioning methods for different roles in the same app?
What's the difference between a resource and a role?
What's the difference between a resource and a role?
Can Serval manage access to Slack channels or Google Groups?
Can Serval manage access to Slack channels or Google Groups?
Do I need to configure every application role in Serval?
Do I need to configure every application role in Serval?
What if an application doesn't have an API or IdP integration?
What if an application doesn't have an API or IdP integration?
Can I set different approval requirements for the same role based on who's requesting?
Can I set different approval requirements for the same role based on who's requesting?
Can users extend their access before it expires?
Can users extend their access before it expires?
Can approvers change the requested duration?
Can approvers change the requested duration?
What happens if a user amends their request before approval?
What happens if a user amends their request before approval?
What happens if no approval procedure is configured?
What happens if no approval procedure is configured?

