Common Review Use Cases
Access reviews answer critical security and compliance questions:- Review which users received JIT access to applications
- Track when access was granted or revoked
- Export access logs for SOC 2, ISO 27001, or other compliance audits
- Track access anomalies or policy violations
- Review departing employee access history to verify all permissions were revoked
- Generate JIT access reports for compliance frameworks
- Identify frequently requested roles and analyze whether temporary access is extended unnecessarily
Review Access by Role
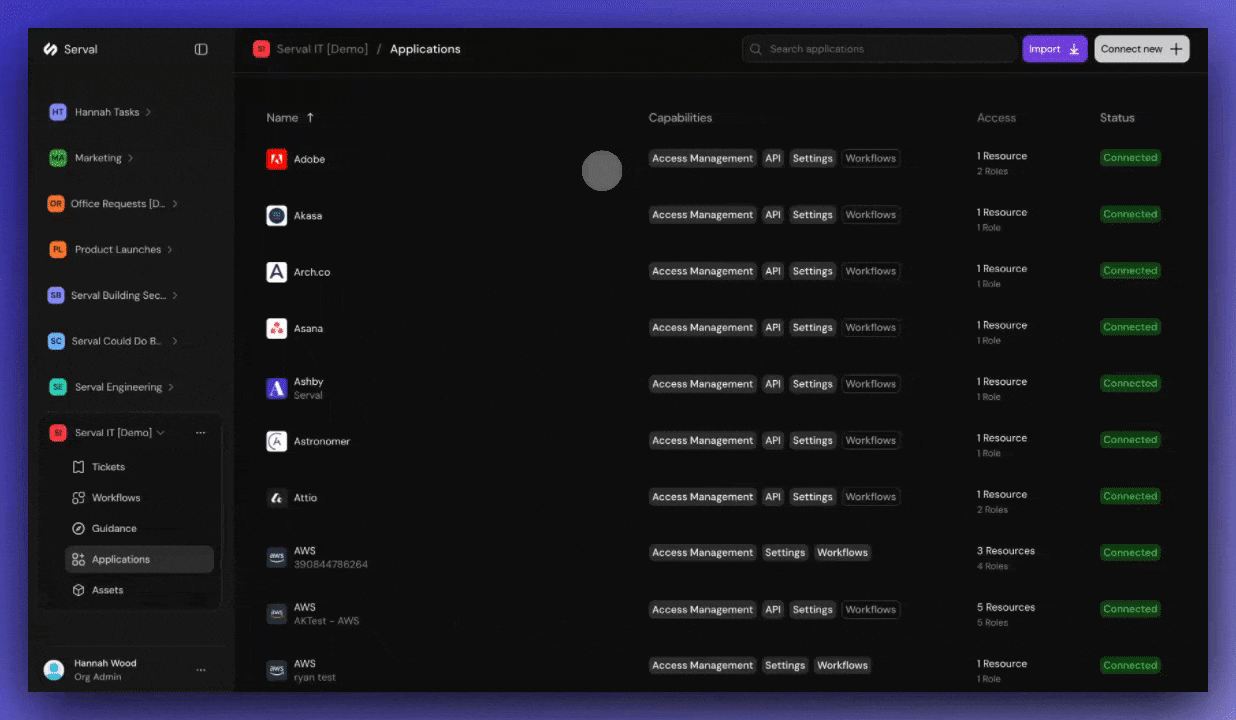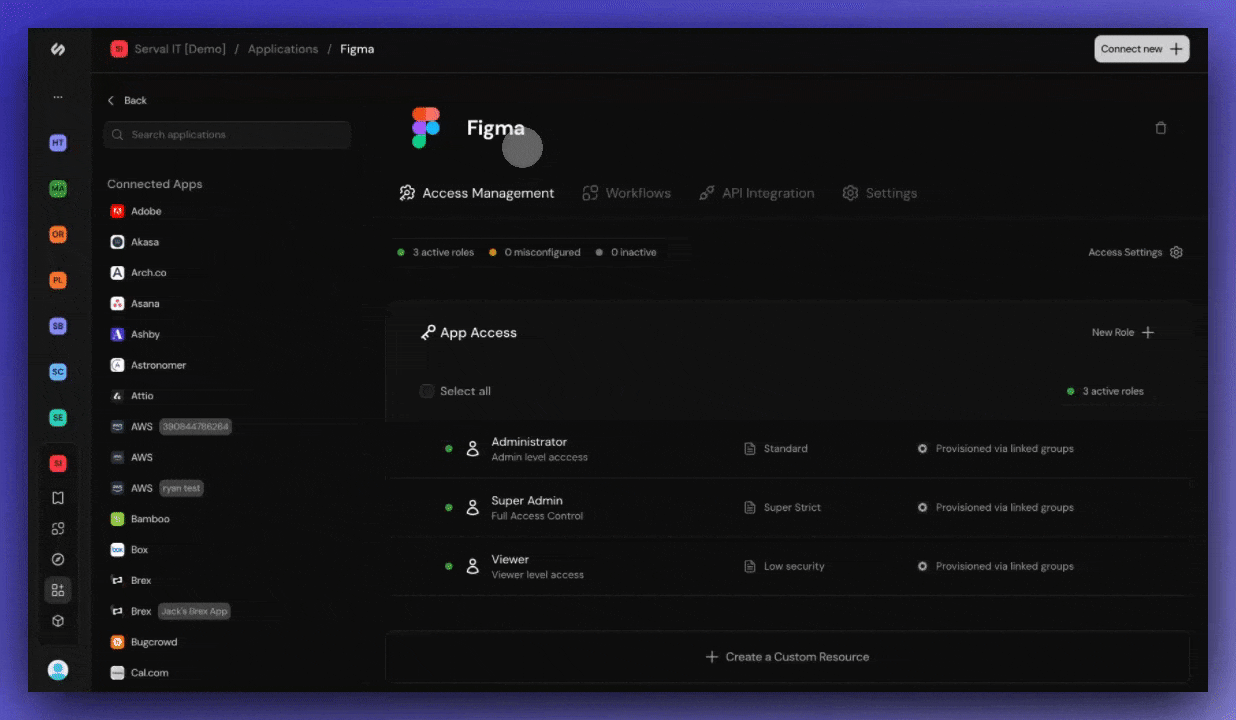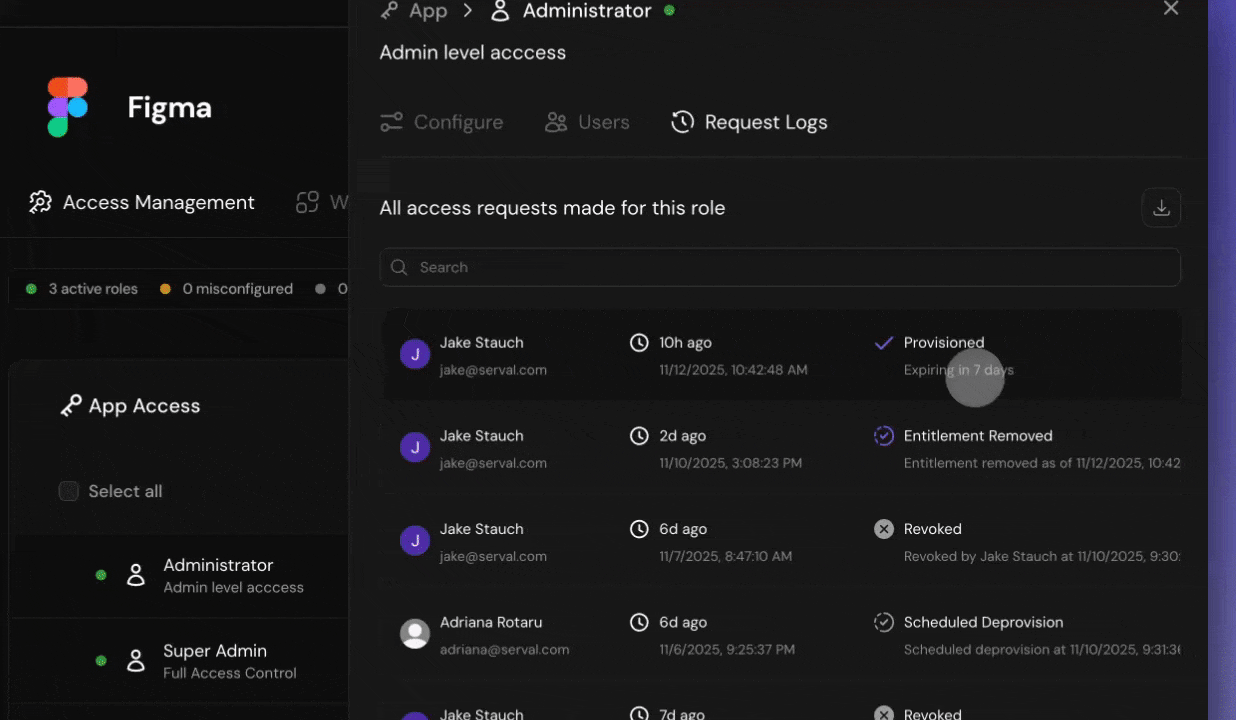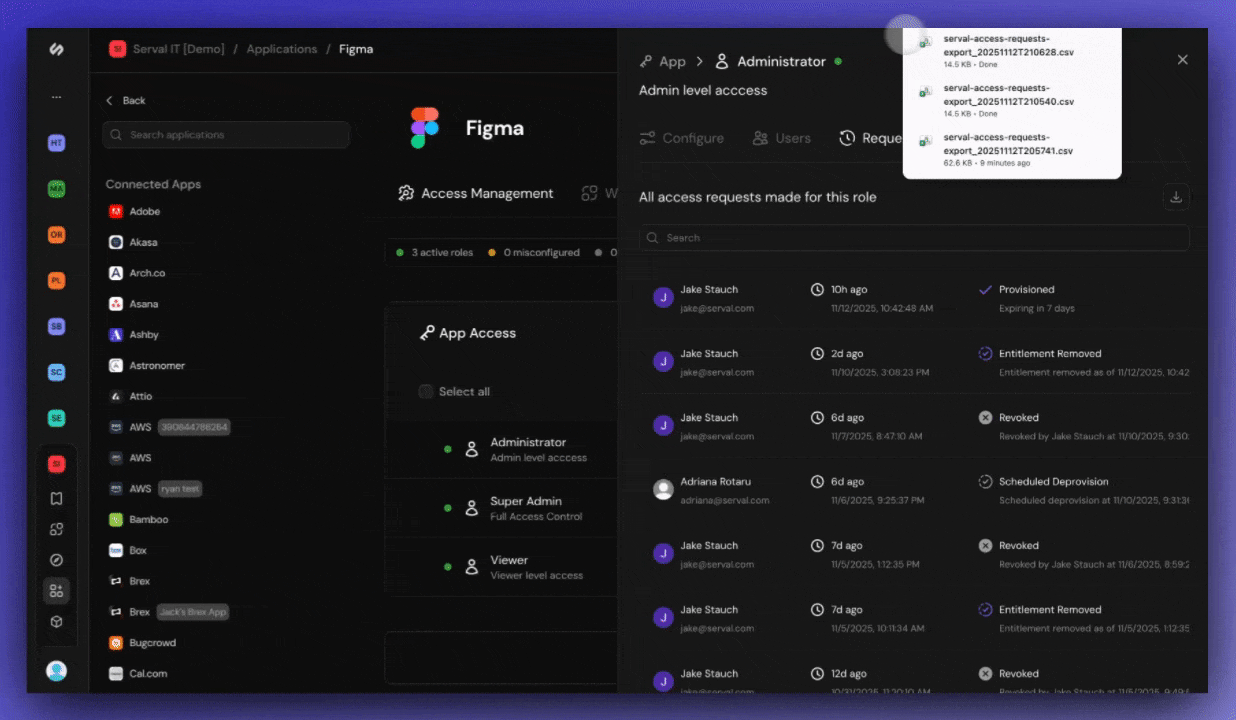
View all users who have been provisioned access to a specific role, including both current and historical access.Access role-level logs
Review access history
The logs show:
- Users with current access
- Users who previously had access
- When access was granted and revoked
- Who approved each request
What’s included in role-level logs
The download includes:- User name and email
- Access start and end dates
- Request and approval timestamps
- Approver information
- Access status (active, expired, revoked)
Review Access Across Teams
Generate comprehensive access reports across all applications and roles in your organization.Access organization-wide logs
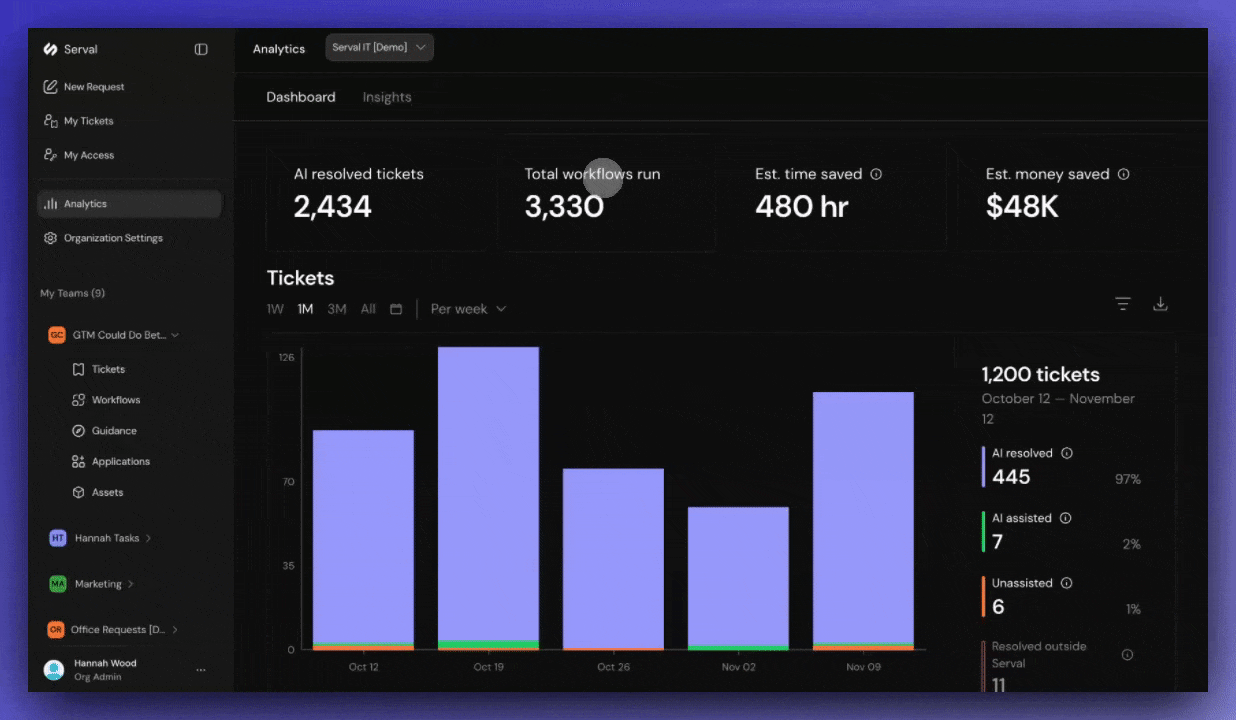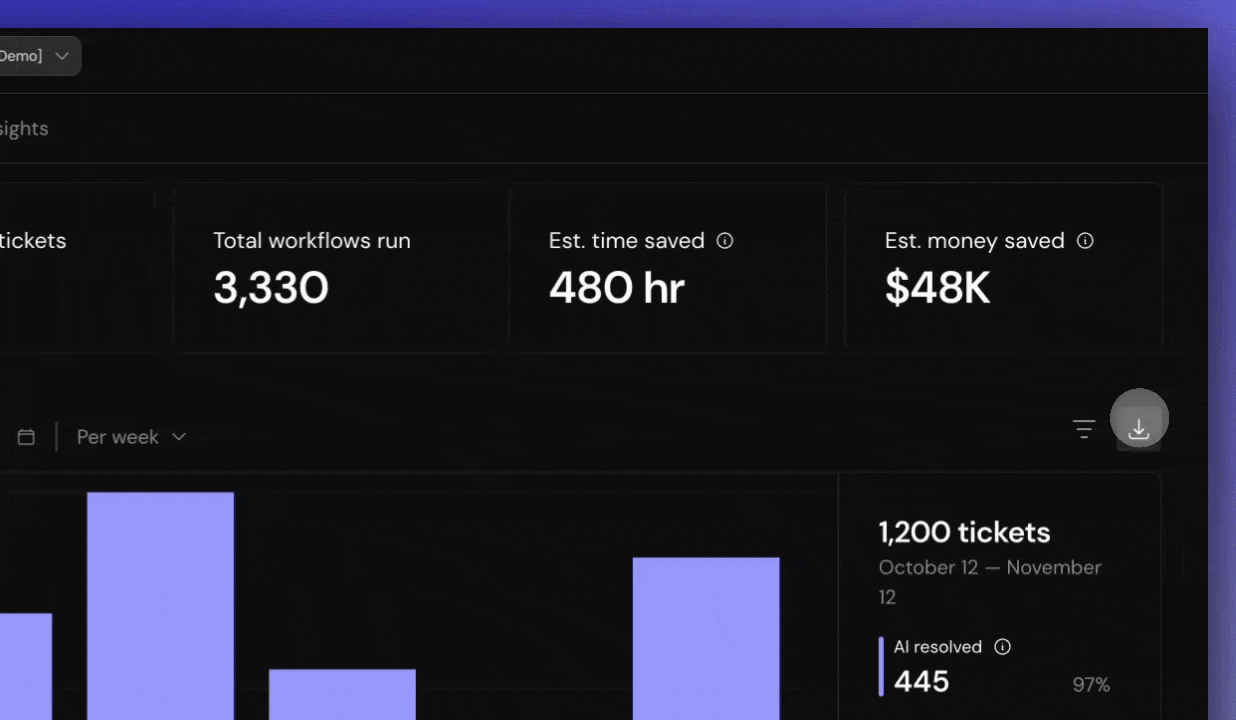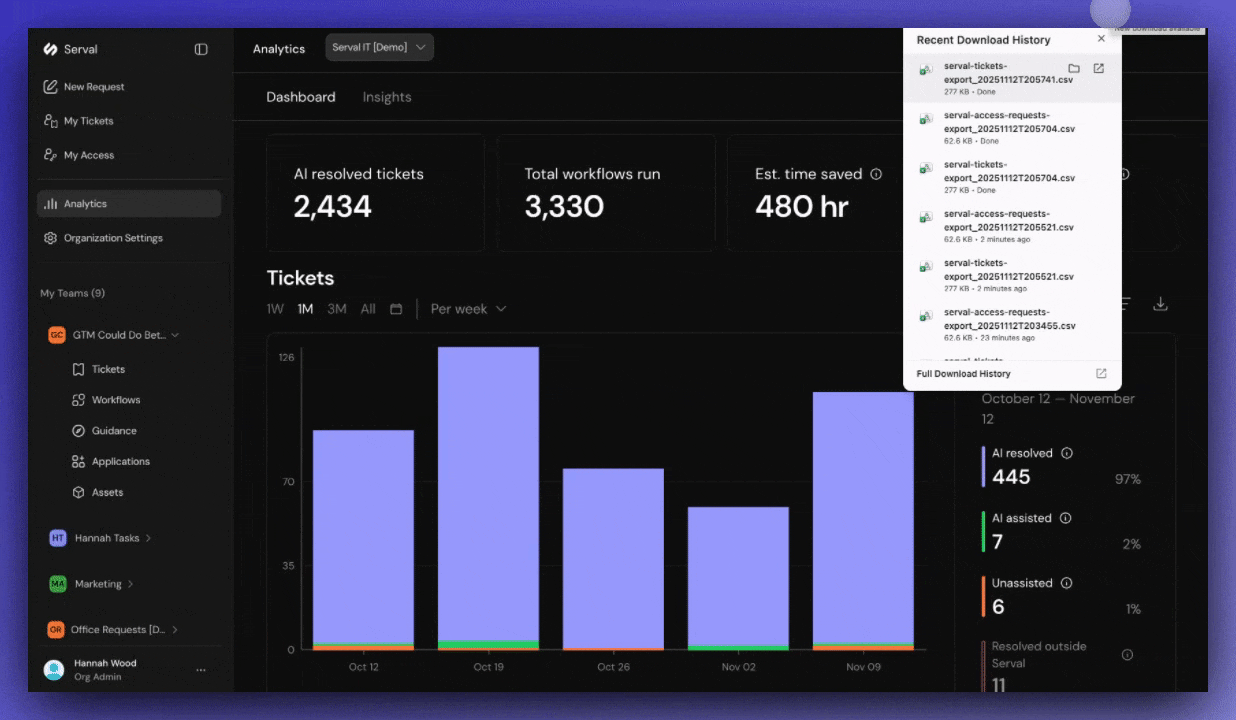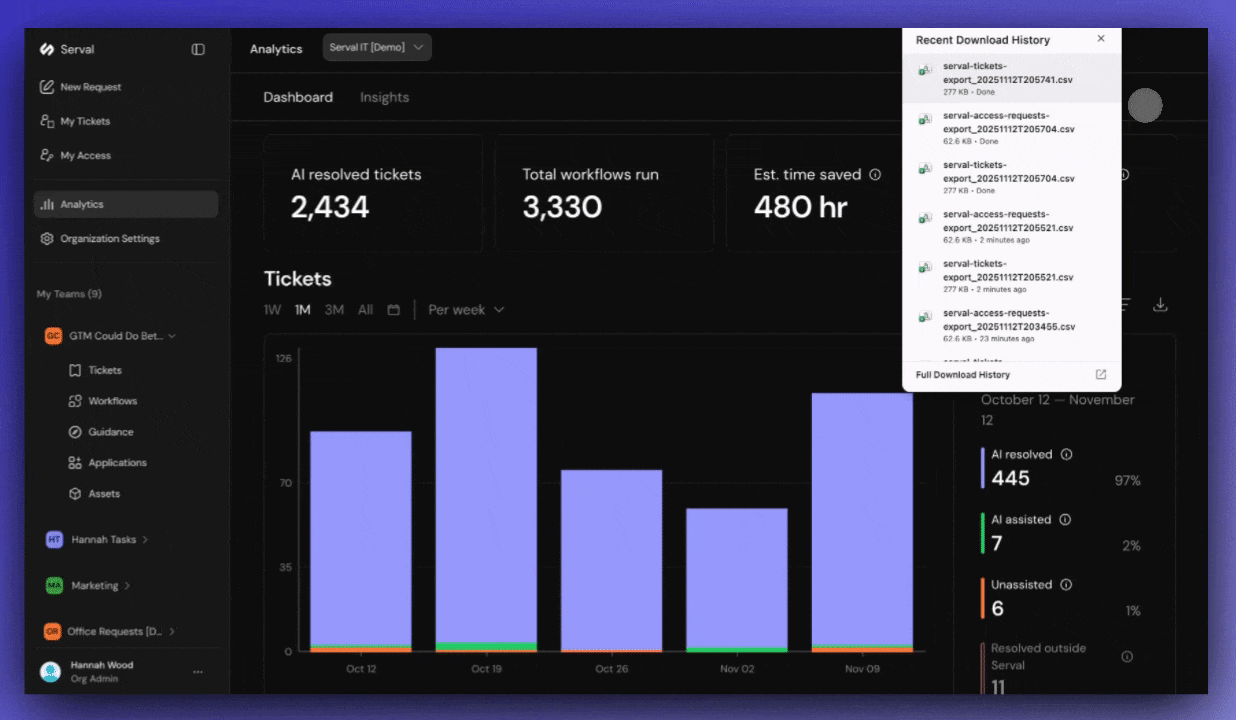
What’s included in organization-wide logs
The export contains the following columns: Ticket information- Ticket ID, Ticket Number, Team
- Ticket Name, Description
- Created At, Completed At, Escalated At
- Created By, Assigned To
- Status, Escalation Level, Priority
- SLA Started At, SLA Breaches At
- Labels, Workflow Calls, AI Feedback
Automate Access Reviews with Workflows
Build recurring workflows to automate access audits and maintain continuous compliance.Example workflows
Weekly admin access review
Trigger: Every Monday at 9amAction: Export all active admin access, send to security team for review
Monthly compliance report
Trigger: First day of each monthAction: Generate access logs for all applications, send to compliance team
Daily inactive access alert
Trigger: Daily checkAction: Identify users with access but no activity in 90 days, notify managers
Weekly contractor expiration review
Trigger: Every MondayAction: Generate access report for contractors ending within 7 days, notify managers
Building an access review workflow
Set up notifications
Configure who receives the review results (security team, managers, compliance)
Best Practices
Review sensitive access frequently
Admin and production access should be reviewed weekly or monthly. Standard user access can be reviewed quarterly.
Export logs regularly
Download access logs even if you’re not actively auditing. This creates a historical record for compliance.
Automate where possible
Use workflows to generate reports automatically. This ensures reviews happen consistently without manual effort.
Act on findings quickly
When reviews reveal unexpected access, revoke it immediately and investigate how it was granted.
Document review processes
Write down your review cadence and who’s responsible. This helps during audits and ensures nothing falls through the cracks.
Track trends over time
Compare access logs month-over-month to identify growing security risks or opportunities to tighten controls.
Supports Compliance Frameworks
Serval can be used to satisfy requirements for common compliance frameworks:SOC 2 Type II
SOC 2 Type II
Requirement: Regular access reviews and documentation of access controlsHow Serval helps:
- Export access logs as audit evidence
- Demonstrate that access is reviewed regularly
- Show that access is granted based on policies
- Prove that temporary access is automatically revoked
ISO 27001
ISO 27001
Requirement: Access control policy and regular access rights reviewsHow Serval helps:
- Document access policies for each role
- Generate access reports for periodic reviews
- Track all changes to access permissions
- Maintain audit trail of approvals
GDPR
GDPR
Requirement: Demonstrate appropriate technical and organizational measures for data accessHow Serval helps:
- Show who has access to systems containing personal data
- Prove access is limited to authorized individuals
- Document justifications for access requests
- Track when access is granted and revoked

